C++ Windows Querying Process Modules
Processes in Windows are made up of "modules" where your executable is your main module followed by any dlls. Common modules include dlls such as user32 and ntdll, and perhaps for older games you'll see glide and ddraw. When memory hacking these modules, it useful to know where they are loaded and how to iterate over their regions - perhaps for a byte pattern scan. For instance if there's a function defined somewhere in "client.exe" and you know the cdecl subroutine signature - then using EnumProcessModulesEx would help you find where that function is without iterating over every single region for every single module in memory.
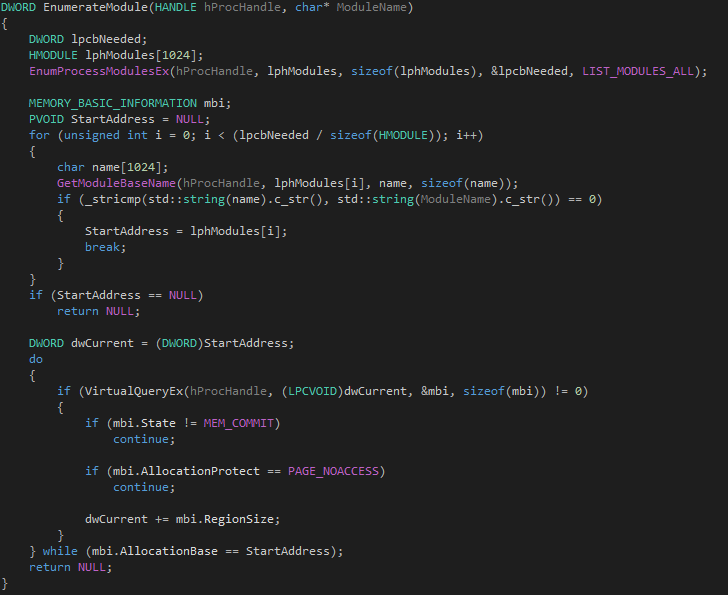
Above is my implementation of an enumeration function which takes in a handle to the process and the name of the module.
In the case of PAGE_NOACCESS, the process can be opened with PROCESS_VM_OPERATION permissions and a VirtualProtectEx call
can modify the allocation protection:
VirtualProtectEx(handle, (LPVOID)dwCurrent, sizeof(mbi.RegionSize), PAGE_EXECUTE_READWRITE, NULL);